Microsoft Office
When it comes to PC software, probably the most used set of tools is Microsoft Office. The software comes with a variety of applications that can be useful to home, school, and business users alike.
Keep in mind that most of these applications are available as web apps as well, so we do our best to make guides for web versions as well.
Since Outlook is the most software from the Office suite, we also have a special section of Outlook guides for our readers.
If you want a guide for specific software, be sure to choose one of the many categories available below.

How to Create and Format a Microsoft Word Table of Contents
How to Accept All Changes on Microsoft Word
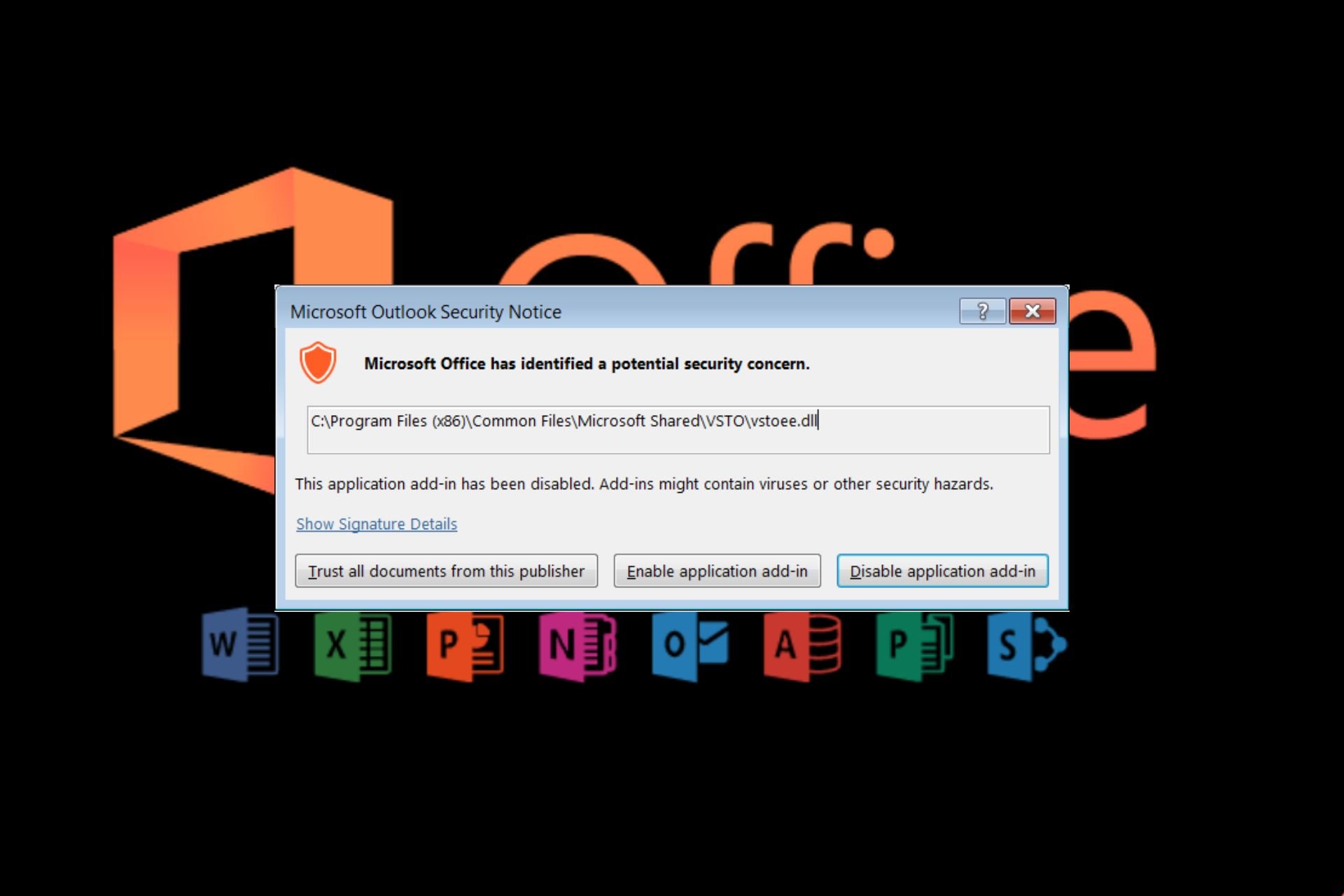
Solved: Microsoft Office Has Identified a Potential Security Concern
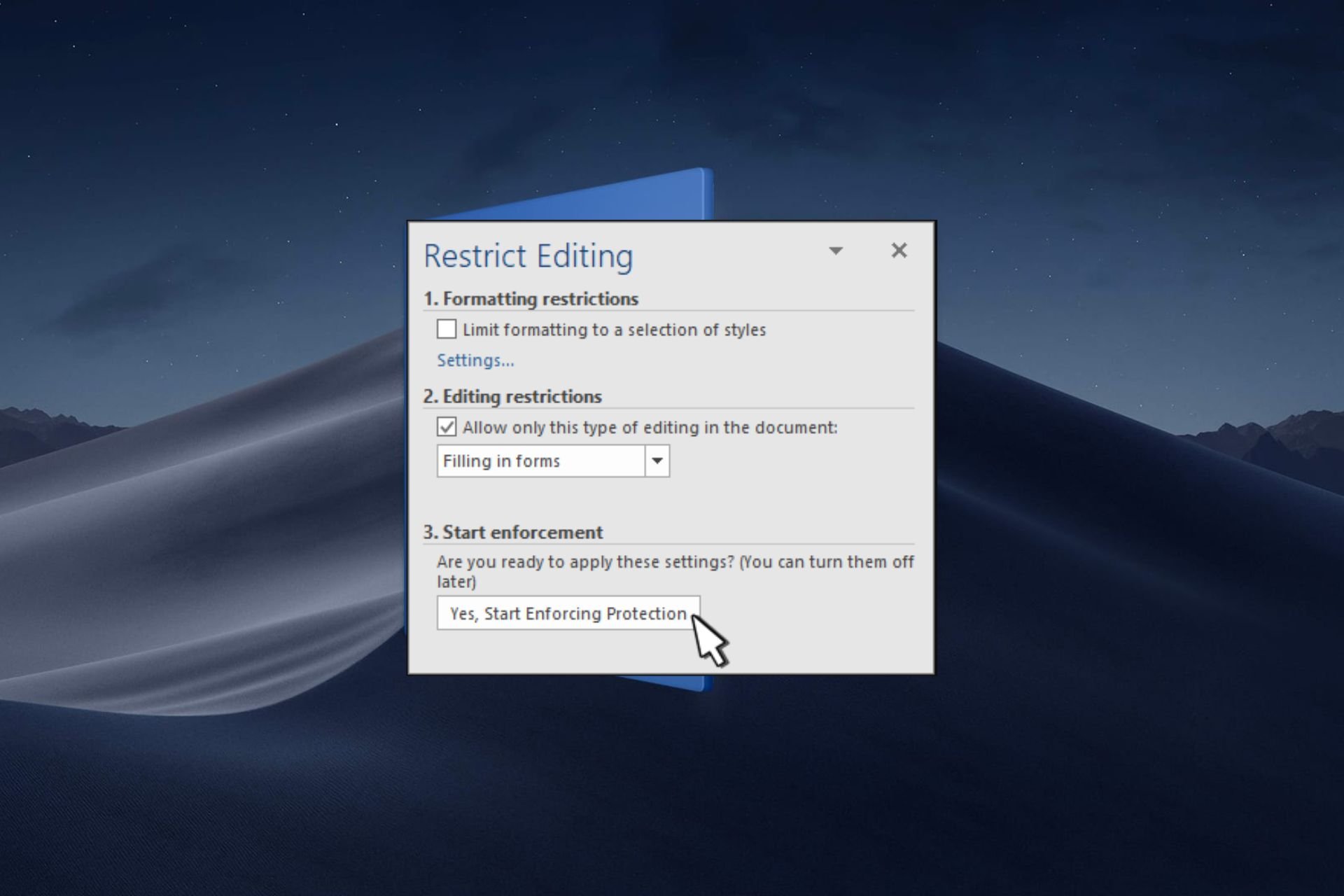
How to Create A Microsoft Word Fillable Form
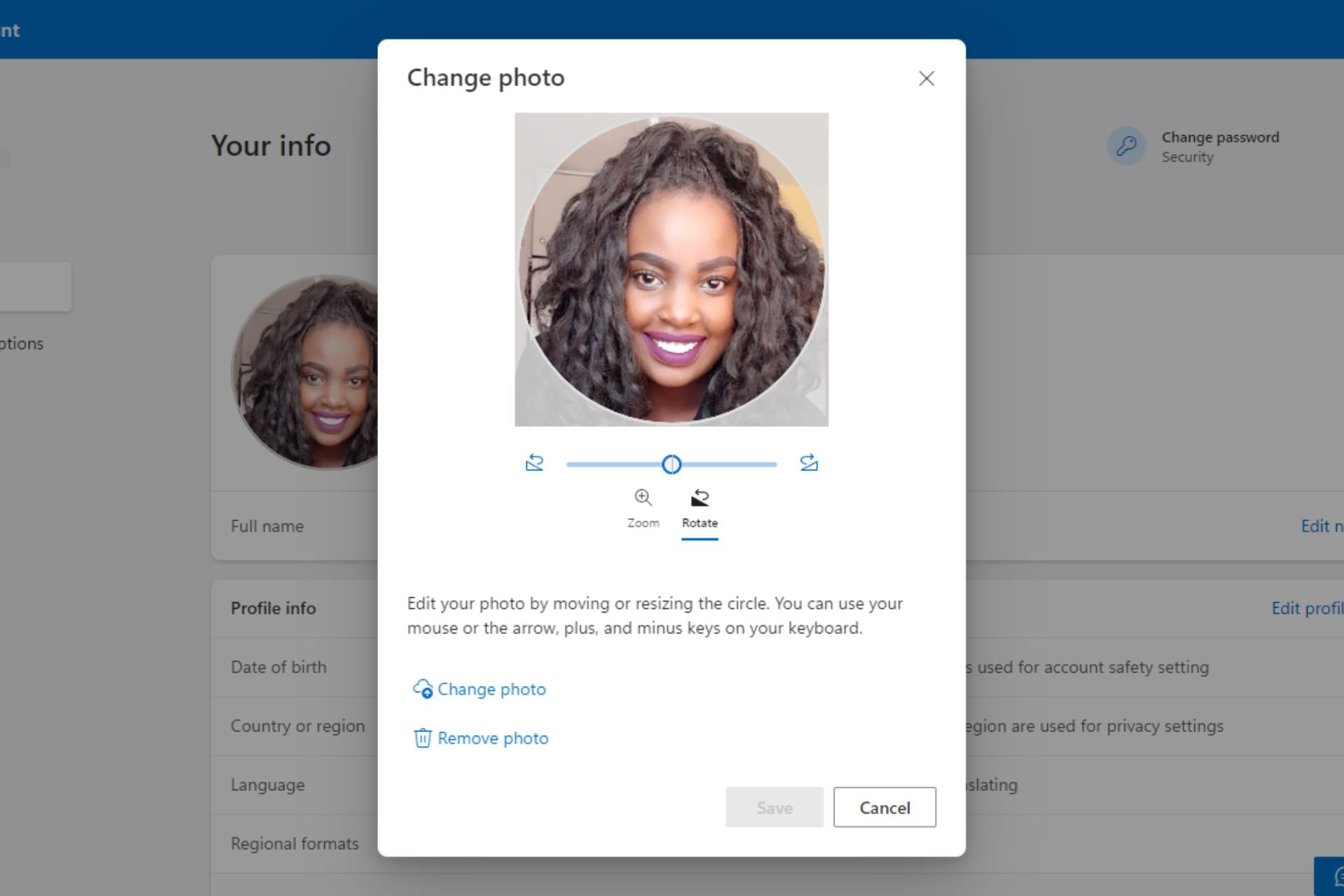
How to Change Your Profile Picture in Microsoft 365
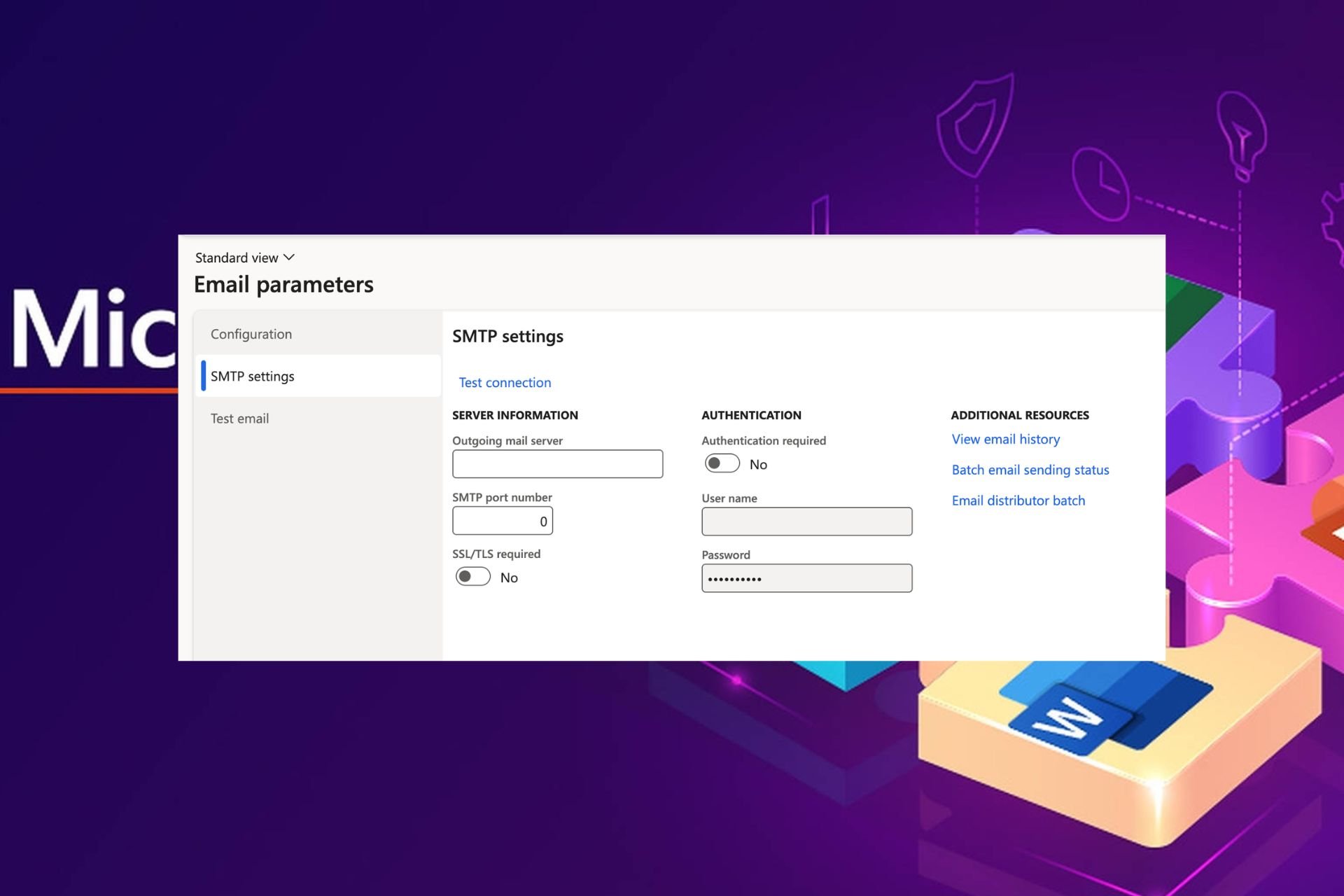
How to Set up the SMTP Server For Office 365
How to Turn On Microsoft Word Dark Mode
How to Put Microsoft Word Header on First Page Only
How to Use The Office Customization Tool
![How to Download Apps From Office 365 [Simple Steps]](https://cdn.windowsreport.com/wp-content/uploads/2024/02/office-365.png)
How to Download Apps From Office 365 [Simple Steps]
Fix: Updating Office Please Wait a Moment Error
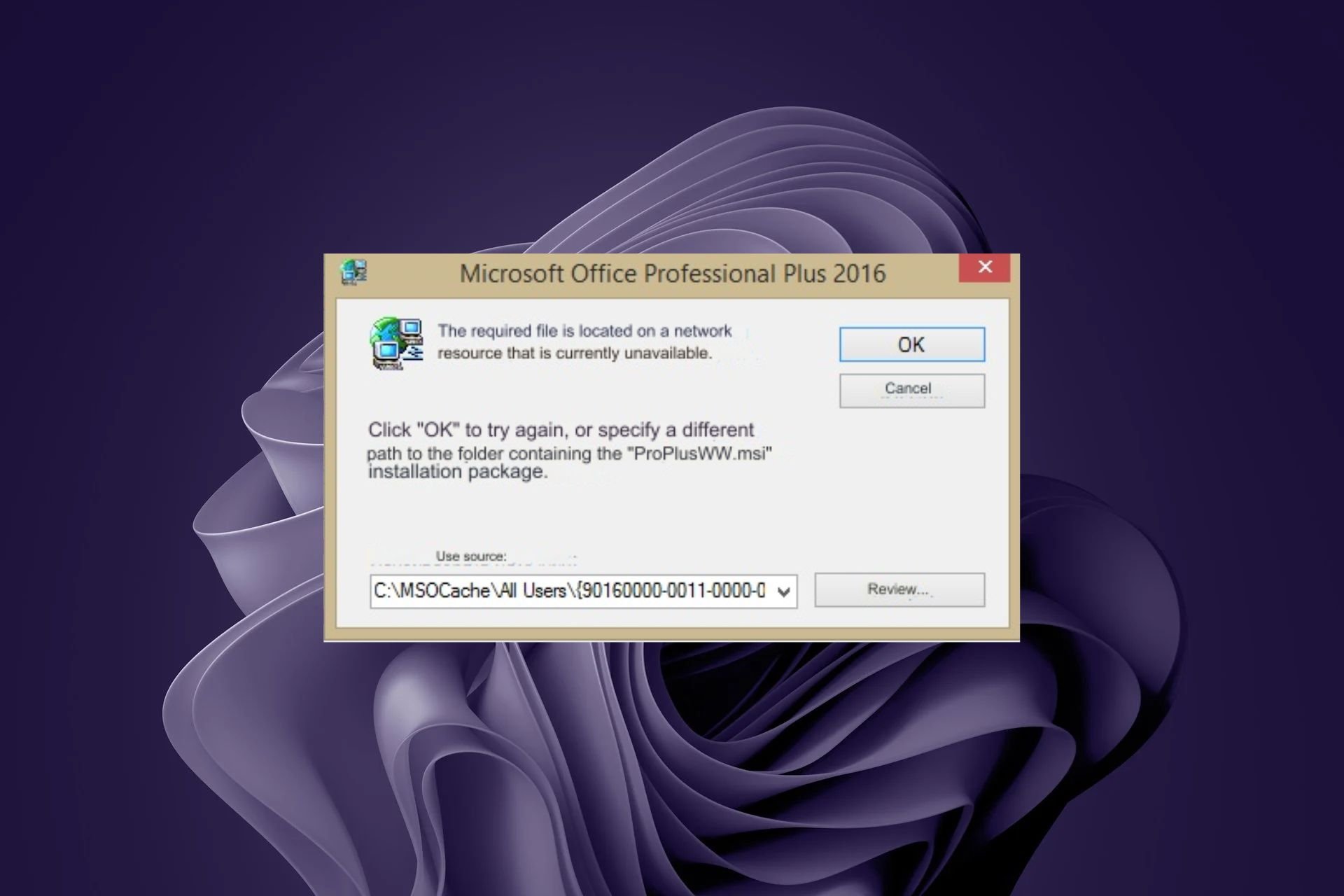
What is Proplusww.msi and How to Fix Its Errors
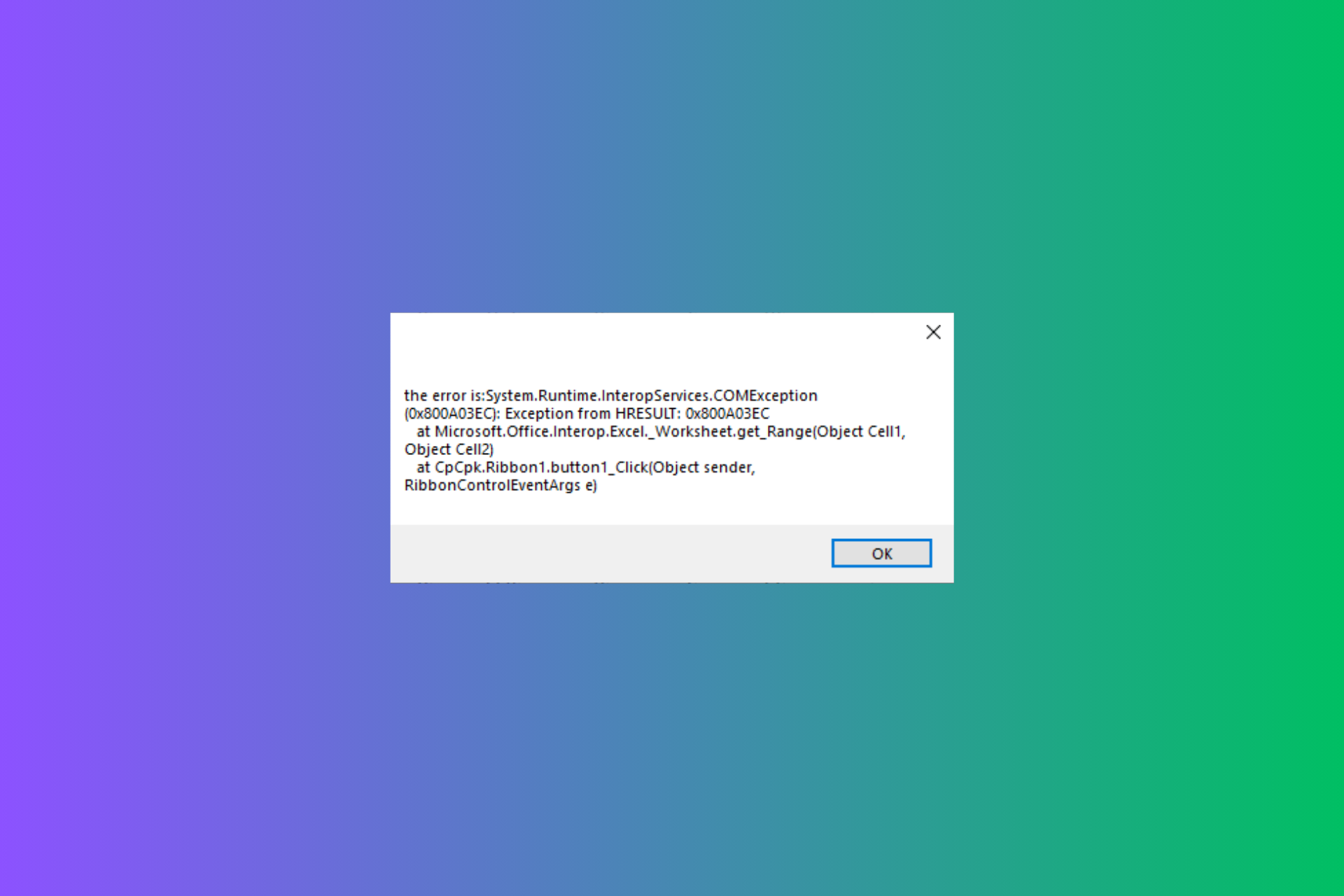
How to Fix The Exception From HRESULT 0x800a03ec Error
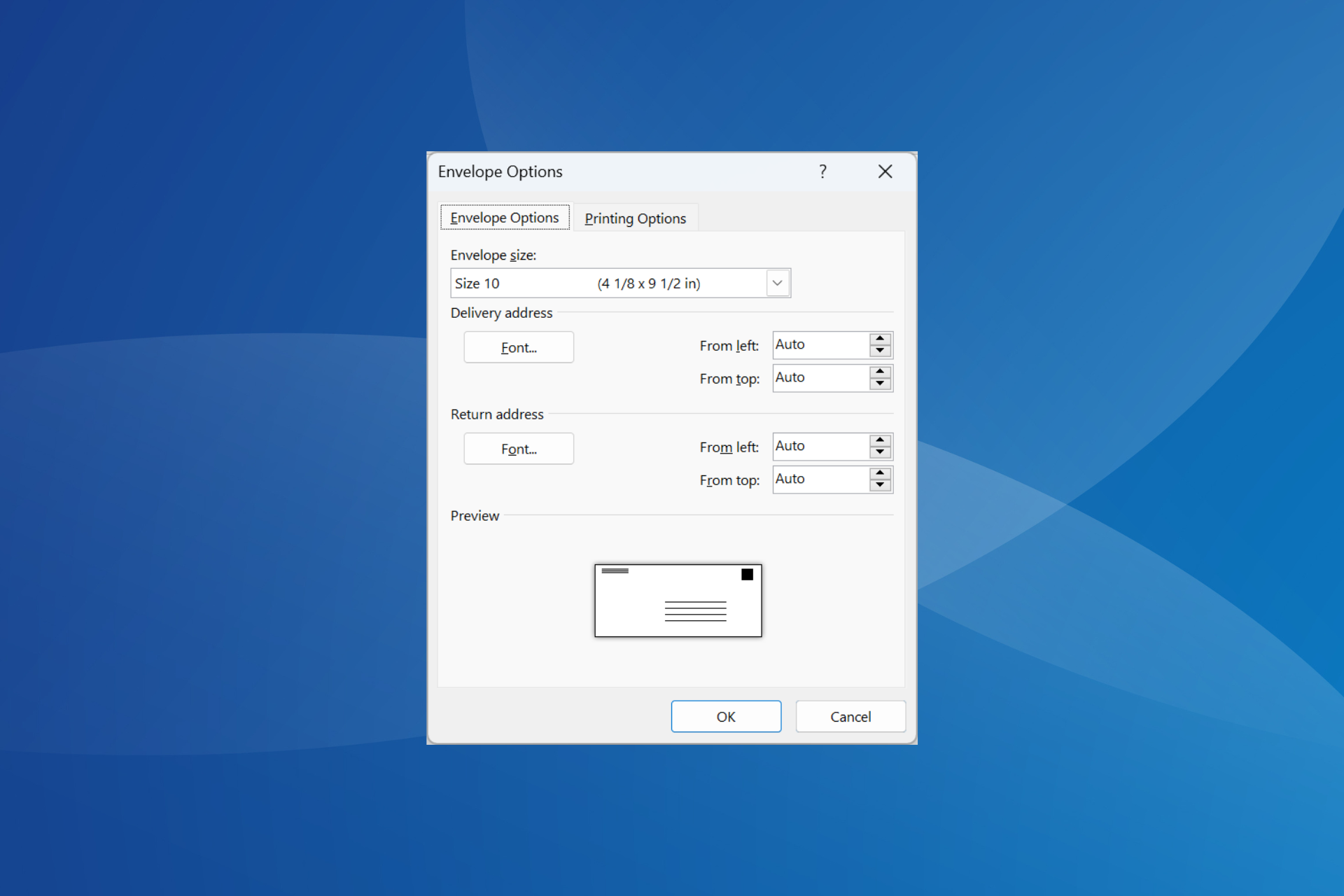
Word Mail Merge Envelopes Not Printing: 5 Ways to Fix it
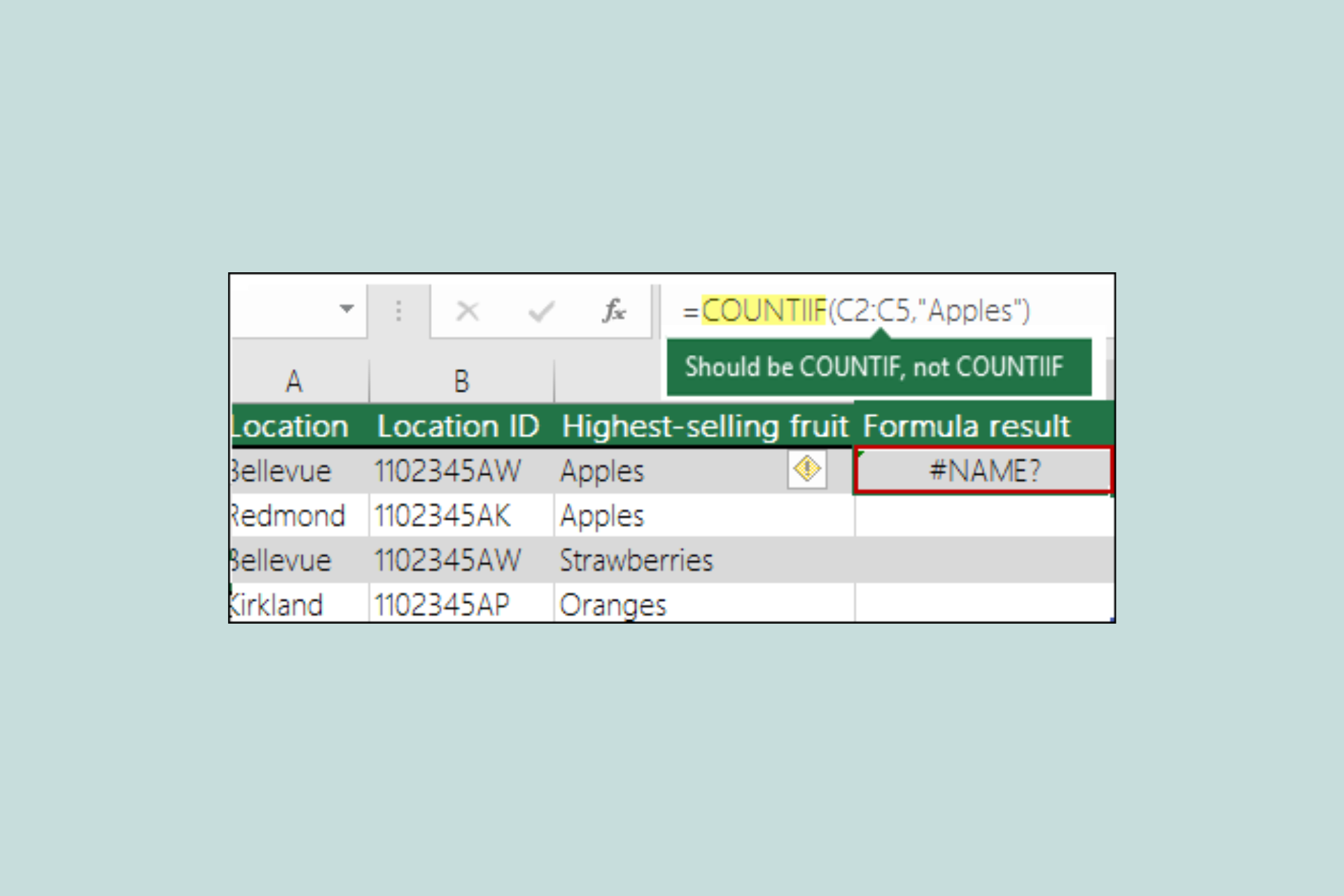
How to Fix the #NAME Error in Excel
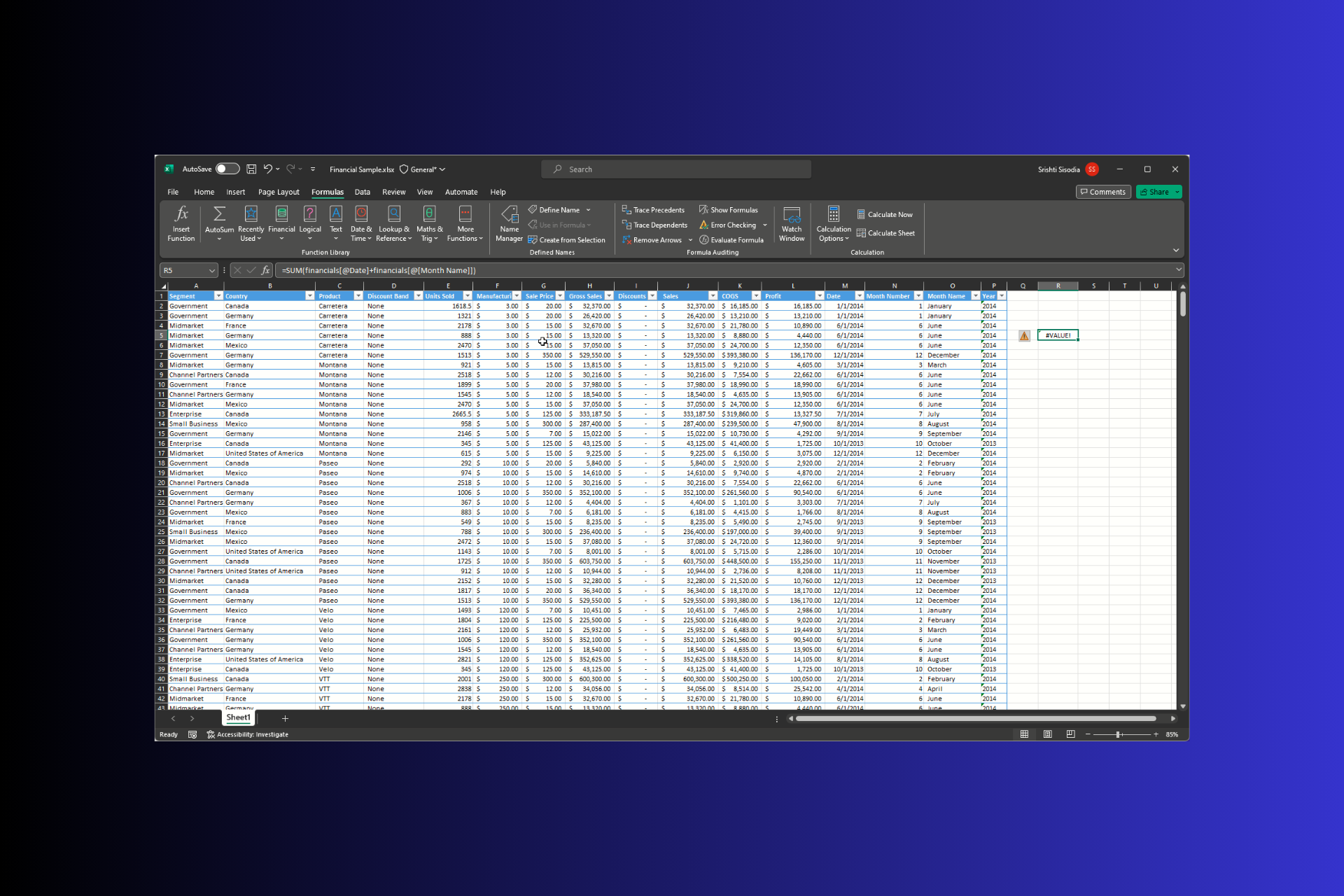
#VALUE Error in Excel: How to Fix it
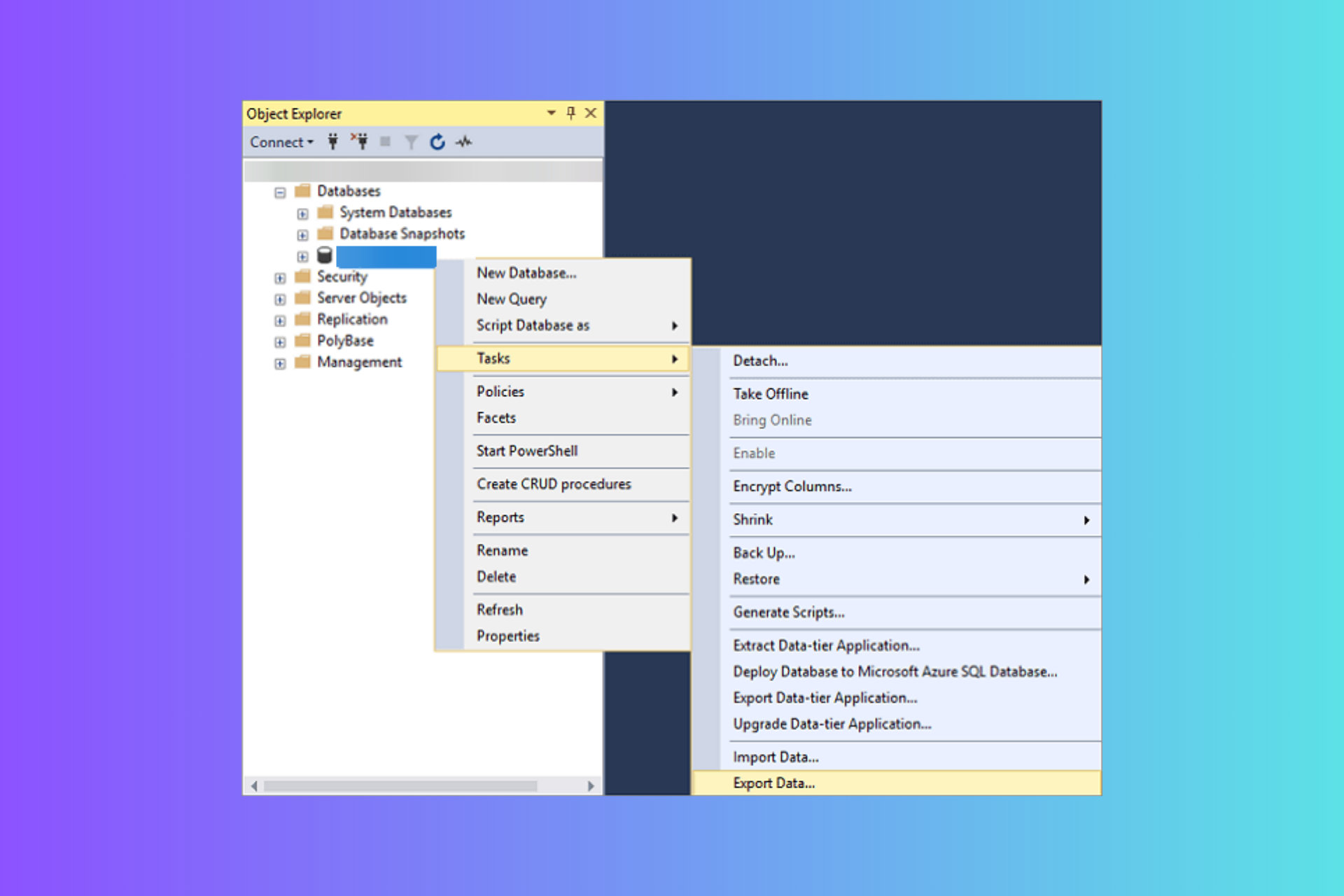
How to Open the SQL .BAK Files in Excel
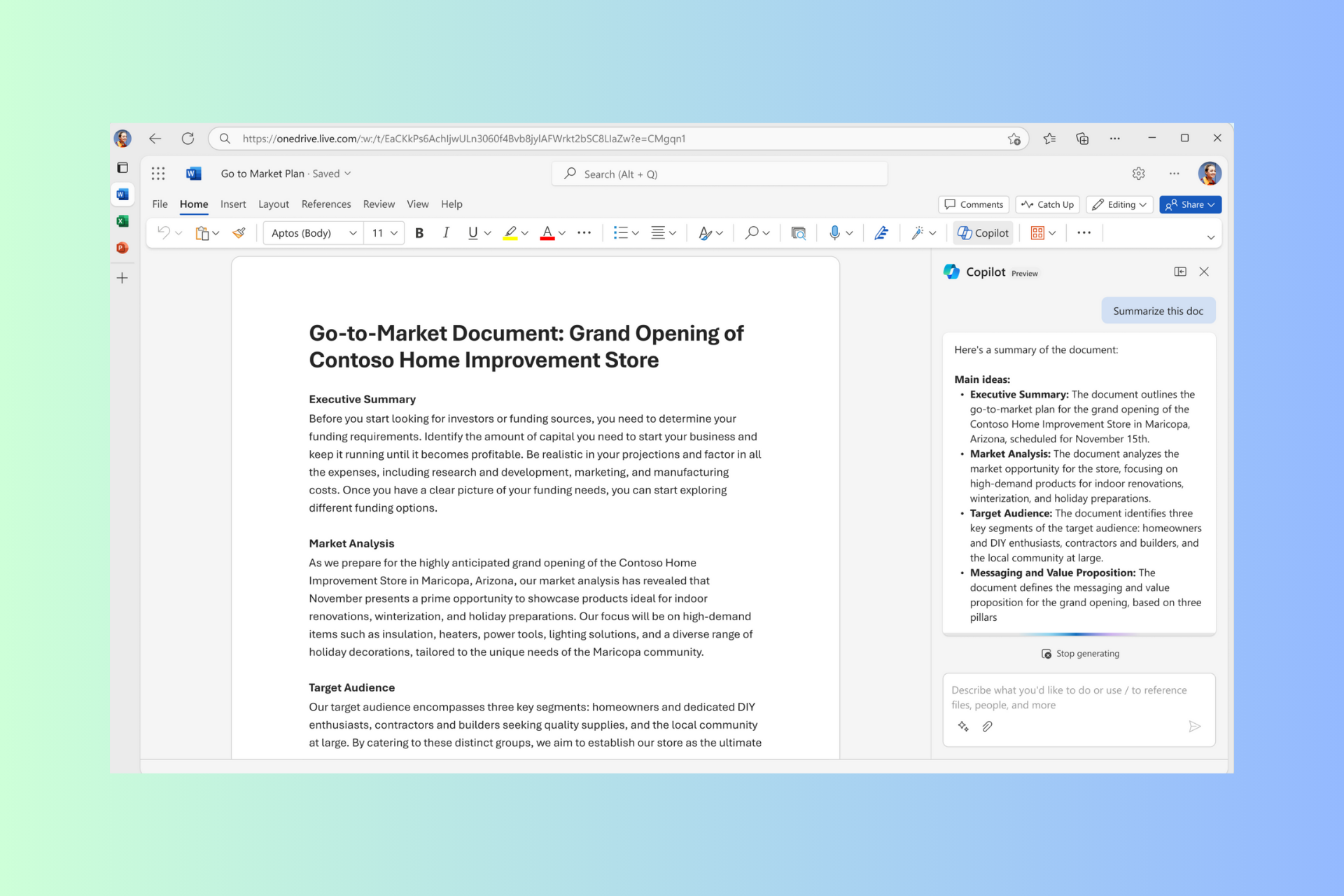
How to Enable & Use Microsoft Copilot in Word

Get Office 365 Lifetime Subscription: How it Works
How to Delete Documents in Microsoft 365
How to Download & Install New Microsoft Office Fonts
Fix: Keyboard Shortcuts are Not Working in Excel
Fix: Keyboard Shortcuts are Not Working in Word
Copilot is Not Available in Your Location? Here’s What to do
Edit Response After Submission in MS Forms [How to]
Download Did Not Complete in Excel: How to Fix This Error
Word is Automatically Deleting Text? Stop it in 6 Steps
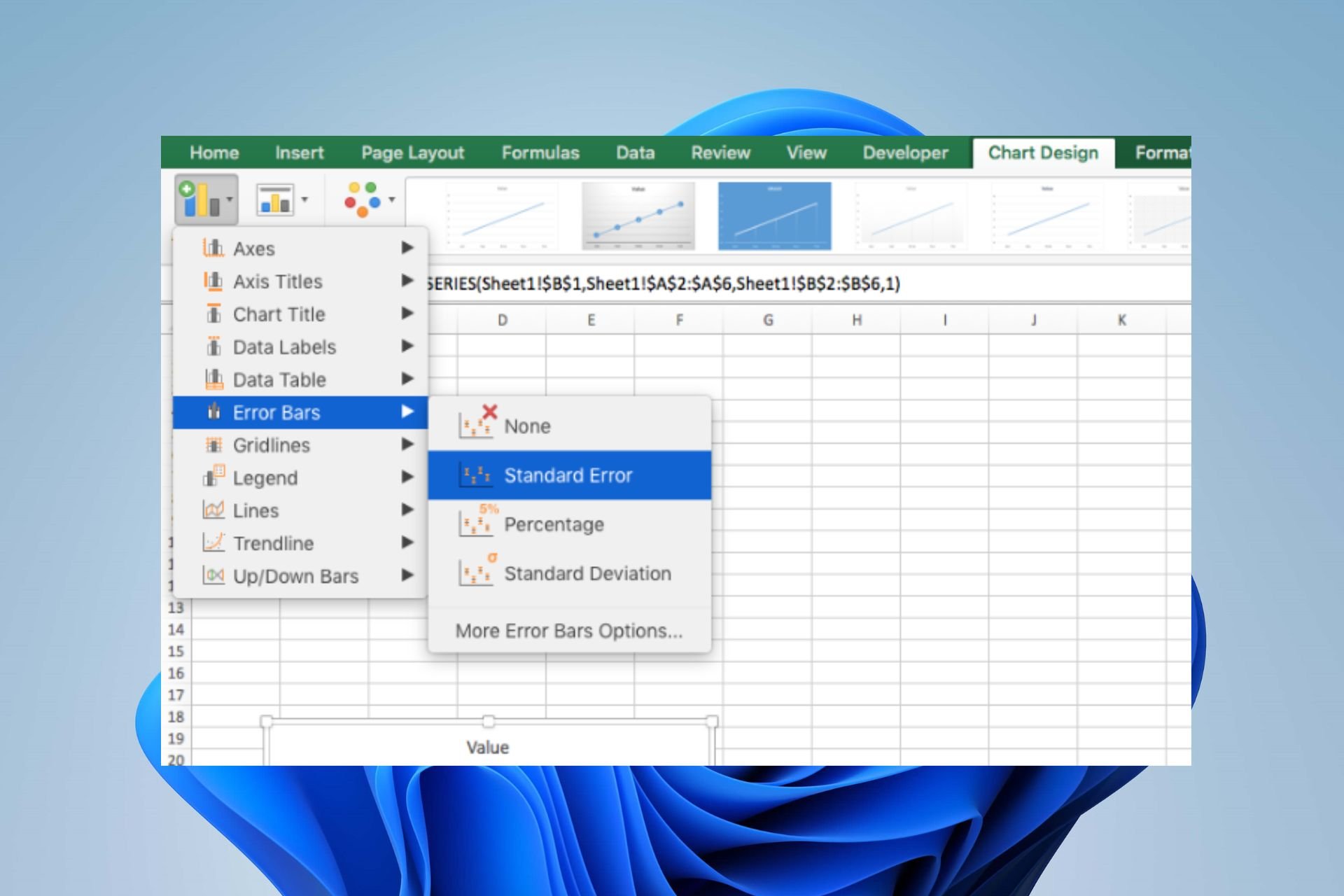
How to Quickly Add Error Bars in Excel [Standard, Custom]
You Need to Sign in With an Account Associated [Excel Fix]
2 Quick Ways to Turn Off AutoFit in PowerPoint
How to Fix Read Aloud in Microsoft Word is not Working
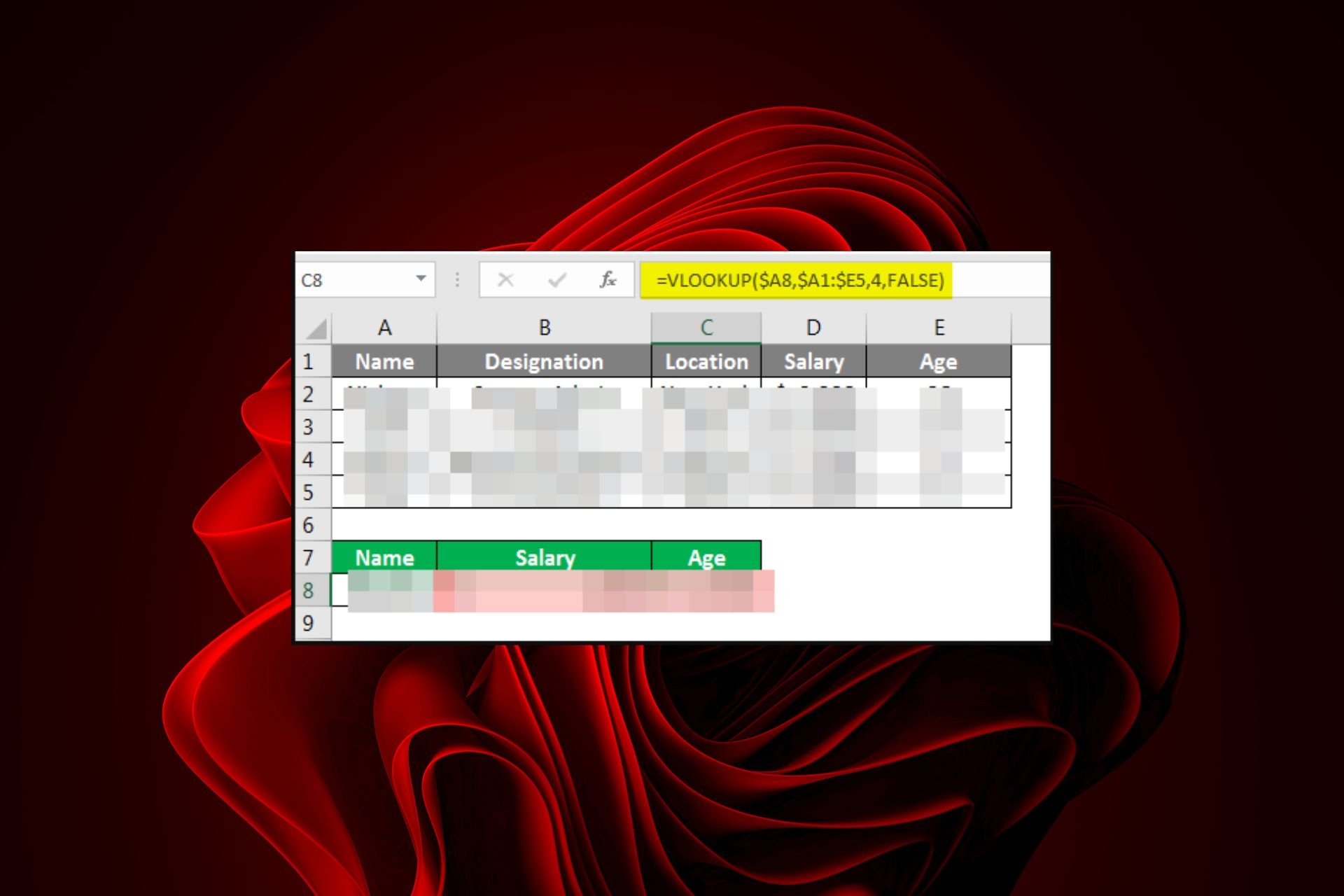
Xlookup vs Vlookup: Why Use One Over the Other?
How to Remove Encryption From Excel [Quickest Ways]
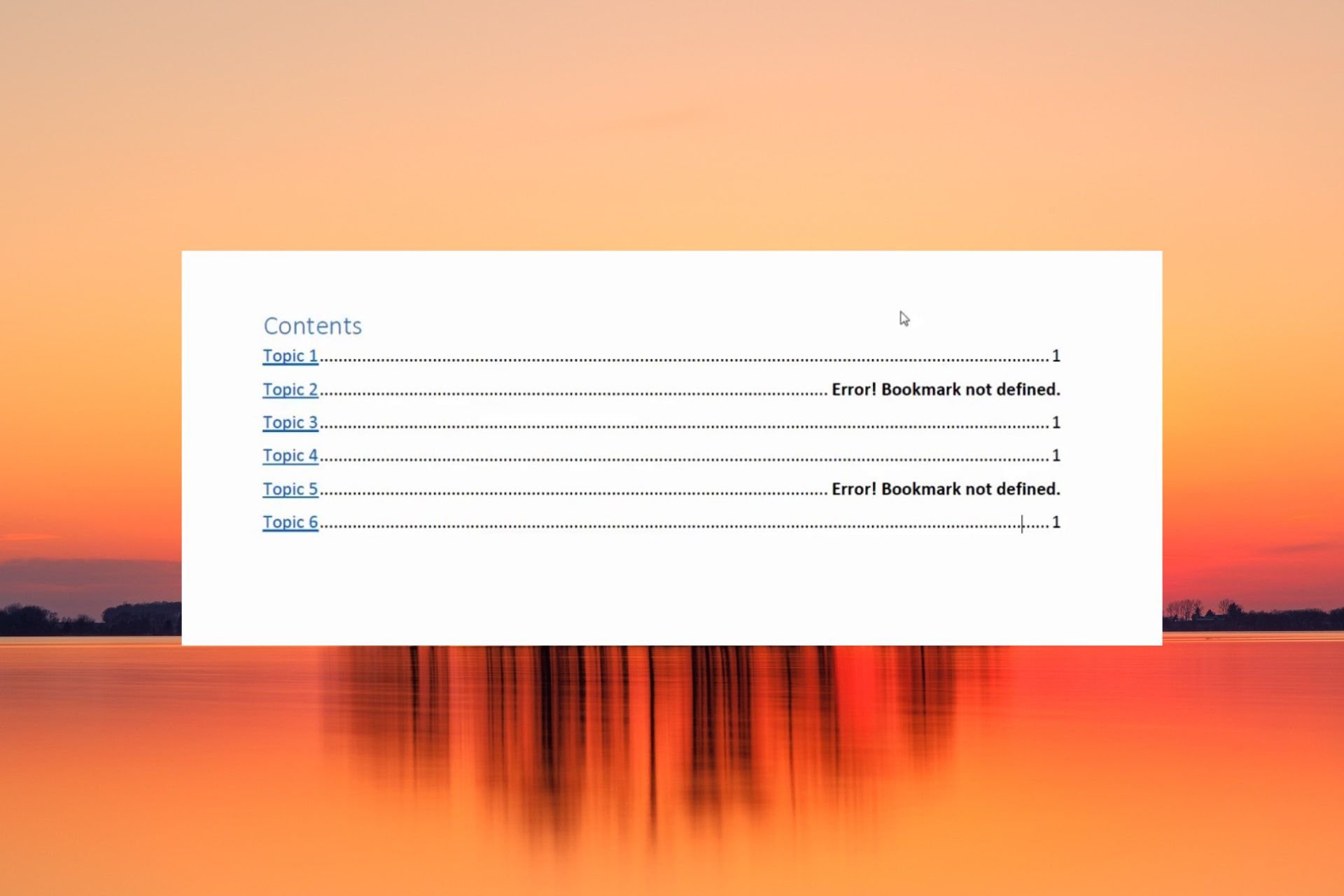
Bookmark Not Defined Error on Microsoft Word [Fix]